So you got that shiny new Netbook, installed Linux on it and carry
it along everywhere you go. The default enabled Firewall blocks
incoming traffic so you feel safe when connecting to that anonymous
WiFi network at your favorite fastfood restaurant. Unfortunately the
very same Firewall becomes quite annoying at home where it prevents
your system from discovering printers or blocks ssh.
You have the choice of either opening the ports permanently,
exposing your system in hostile networks, or having to use sudo to
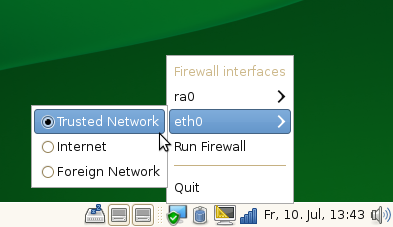
enable or disable the Firewall. Well, not anymore with Firewall Zone
Switcher! With that little applet you can now switch the zone of
your network interface to ‘internal’ with only two mouse clicks when
you are at home. In an untrusted Network you just set the zone to
‘external’. And if you need some custom configuration you could set
the zone ‘dmz’ to have some open some ports or create a custom zone.
Firewall Zone Switcher is *not* meant to be some kind of ‘Personal
Firewall’ that confuses the user with all kinds of low level stuff.
It’s neither a Firewall configuration tool. That job is still left
to Admin tools like YaST. Firewall Zone Switcher settings are
temporary and are reset to the system defaults on reboot.
Firewall Zone Switcher consist of a DBus service and a system
tray applet. Both are written in python currently to have proof of
concept program quickly. Packages are available from the openSUSE
build service. You also need to update SuSEfirewall2 from that
repo. Source code repo is available at gitorious.
Keep in mind that the app as well as the patch to SuSEfirewall2 are just proof
of concept ie experimental so there will be bugs. Feedback welcome nevertheless
🙂
Both comments and pings are currently closed.
oooh this looks just what the doctor ordered, simple but so usefull ! thanks !!
Move proof-of-concept to NetworkManager. Just not to make a tray-mess like in Windows 😉 .
I wonder if firewall configuration for Samba could work… Currently Samba makes user need to do manual firewall config. Add IPs, enable broadcast…
Yes, connecting this to NetworkManager would be nice. Esp since
NetworkManager knows when it is about to start a new connection so
it can prepare SuSEfirewall2 already before the interface is set up.
Enhancements for samba are already implemented and will be available
as online update soon. The SuSEfirewall2 version in the fwzs repo
has those enhancements too.
Hmm, food for the D-Bus junkie!
It looks like this is the git repo. (Still empty so far)
Ideal UI suggestion — Have a property of a wifi network to be ‘safe’ in NM’s ‘edit connections’ and have NM turn off the firewall automatically. No need to expose any UI for switching and polluting the systray with yet another icon.
yes 🙂
When did SuSE move to creating GNOME apps/applets? I thought it was a KDE-focused distro. Shame, seems to me that SuSE is trying to out-do Ubuntu with the same limited interface.
It’s not openSUSE, it is Novell who’s GNOME-focused. Even though they’re still patrons of KDE, they still have a lot of KDE devs and they still implement KDE very well, GNOME has taken KDE’s place especially in SLED. Look at iFolder. AFAIK it is written using mono and Gtk#. Even though it is not a gnome library, you know which DE you’re targetting if you write an app with Gtk# and where it’ll fit the best. The same applies to banshee, f-spot and tomboy. Furthermore, they sponsor OpenOffice.org and Evolution (and this one is a GNOME app). However Novell doesn’t sponsor a KDE app or a qt app (except yast, of course). They sponsor KDE as a project (just as they sponsor GNOME as a project), but not individual apps. I hope in the future Novell will develop an app using mono and qt (which is perfectly possible) or will sponsor a qt/KDE app as well (BTW this is not meant to offend anybody or to start a flame war, this is what I see and my opinion and it is perfectly debatable).
As to the feature itself, even if this is shown in gnome, it doesn’t mean the community won’t develop a plasmoid (or won’t add this feature to NM’s plasmoid as suggested by others) and still remains a useful one.
it’s not a gnome app. plain (python-)gtk.
Nice for these who change environment & need diffrent network configurations w/ default OpenSuSE firewall. Though I don’t need diffrent configs – always paranoid. 😉
I also notice you about a bug in previouse report on adding entire drive encryption to Open SuSE from the box here:: //lizards.opensuse.org/2009/03/18/encrypted-root-file-system-on-lvm/. Sorry – comments there seem to be closed.
Value of variable ‘root_luks’ must be device you’ve encription on. In this case root_luks=/dev/sda2 . Value ‘1’ works only when booting from /dev/sda1 & makes me on each boot enter cryptsetup luksOpen /dev/sda2 root & so on.
From this we can guess that with value of curluks ‘root’ the $(eval echo $luks_root) should give /dev/sda2 (or your specific device):
olli@linux-82d5:~> cat /lib/mkinitrd/scripts/boot-luks.sh | grep curluks
for curluks in $luks; do
/sbin/cryptsetup luksOpen $(eval echo \$luks_${curluks}) $curluks
olli@linux-82d5:~>
Also I had trouble with getting initrd w/ luks future by default at least on one of my notebooks (having all done by your howto).
To get this work anyway I found that variable:
olli@linux-82d5:~> grep ADDITIONAL_FEATURES /lib/mkinitrd/scripts/ -r | grep %
/lib/mkinitrd/scripts/setup-prepare.sh:#%param_f: “Features to be enabled when generating initrd.\nAvailable features are:\niscsi, md, mpath, lvm, lvm2, evms” “\”feature list\”” ADDITIONAL_FEATURES
olli@linux-82d5:~>
Also to get the things work I had to modify INITRD_MODULES in sysconfig/kernel – append all crypto modules I needed to cryptsetup luksOpen .
So my configuraation looks now this way:
olli@linux-82d5:~> cat /etc/sysconfig/kernel | grep INITRD_
INITRD_MODULES=”processor thermal ata_piix ata_generic ide_pci_generic fan jbd ext3 dm_mod edd aes_generic arc4 cbc aes-i586 dm_crypt crypto_blkcipher ecb sha256_generic”
DOMU_INITRD_MODULES=”xennet xenblk”
olli@linux-82d5:~> cat /etc/sysconfig/initrd
luks_root=/dev/sda2
luks=root
ADDITIONAL_FEATURES=”luks usb”
olli@linux-82d5:~>
One more mminor notice: within advanced options in GUI for grub installation it is possible to append ‘luks_root=/dev/sda2’, this will lead in appearing this string in all needed strings in sysconfig/bootloader.& save a few seconds. 🙂
Also for those who will use usb keys to boot: I had to use root=(hd0,1) (not hd1,1) w/ grub, since after booting from usb the usb beconmes a 1st drive for grub (in loaded linux it was second for me).
Thanks for your howto, BTW, really – now I can enjoy openSuSE & giveup my tries to find something w/ entire encryption support & good enough for my needs.
Please update howto w/ notices above – after this changes my system is booted from usb key & prompts for password for /dev/sda2 w/o noisy messages & shell prompt. =)