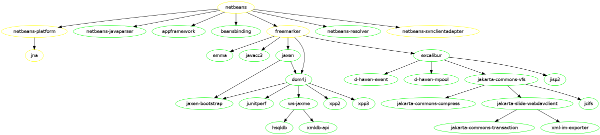
This year I’m going to participate in the Google Summer of Code and my goal for this summer is to add support for oauth to the openSUSE BuildService. My mentor is darix. In the following I’m going to describe the project and its planned implementation a bit further.
oauth is an open protocol which describes the required steps for a client to
authorize with an API. In traditional protocols the client asks for the user’s
credentials (most-likely a pair of an username and password) and uses these
credentials to authenticate with the API. One drawback of this approach is that
the user has to trust the client that it stores the credentials in a secure way
and that it doesn’t misuse it.
oauth tries to solve these issues in a more elegant and secure way.
Small overview about oauth:
Every API (in oauth terminology “Service Provider”) has a list of known clients
which have a unique id (in oauth terminology “Consumer Key” and
“Consumer Secret”). In order to authorize the client and the API exchange so
called “tokens”.
First the client sends its unique id to the API which verifies the id to make
sure that this client is allowed to use the API. If everything is ok the API
sends back a so called Request Token (which isn’t authorized yet).
In the next step the client redirects the user to the API’s login (this request
also includes the formerly received Request Token). This is the most important
point because the user logs into the API with his/her credentials and the
client _never_ gets in touch with the username and password. After the user
logged in he/she has to approve to grant the client access. If the access is
granted the API sends back the authorized Request Token and redirects the user
back to the webclient.
In the last step the webclient exchanges the authorized Request Token for a
so called Access Token. Now the webclient will use the Access Token for all
requests it sends to the API.
The major advantage is that the webclient only knows about the Access Token
and doesn’t have to fool around with the a username and password. So in case
the webclient gets compromised the attacker can just access the API but not
the other services.
The best is to describe the oauth workflow with a small example.
Note: this example is very idealized and its sole purpose is to visualize the rough workflow of the protocol.
Let’s say the BuildService webclient and the BuildService api use the oauth protocol and the
webclient wants to fetch the projectlist:
request projectlist
webclient ——————————————————> API
API realizes that the webclient isn’t authenticated yet and it returns a 401
401
webclient <—————————————————— API
request Request Token
webclient ——————————————————> API
verify client id, send back unauthorized Request Token
webclient <—————————————————— API
redirect user to the API login
webclient ——————————————————> API
user logs in
API <—————————————————–> API
user grant client access
API <—————————————————–> API
send back authorized Request Token
webclient <—————————————————— API
exchange Request Token for Access Token
webclient ——————————————————> API
verify request and send back Access Token
webclient <—————————————————— API
All consecutive webclient requests contain the Access Token
request packagelist (request contains the Access Token)
webclient ——————————————————> API
verify Access Token and send back packagelist
webclient <—————————————————— API
Within the scope of this project my plan is to add basic oauth support to the following components
To do so I might use the following libraries:
So the next step is to investigate how these libraries work and how they can be used for this project. I’ll blog about my investigations – stay tuned 🙂
Ps. feedback, comments etc. are welcome.