Because I feel a tad bit guilty about missing all of the Community Week sessions this week (school and work training, and before you ask, I’ve got more training all this weekend, so I can’t make those sessions either), I did decide to do a quick tour of the GNOME Shell, one of the integral parts of the GNOME 3 series, scheduled to be coming out in 2010 or so.
First, big thanks to Vincent Untz for packaging the GNOME Shell packages for openSUSE! I’m using these packages for my testing purposes
Here’s the quick tour:
First, here’s the openSUSE 11.1 desktop w/ GNOME 2.24 running GNOME Shell:
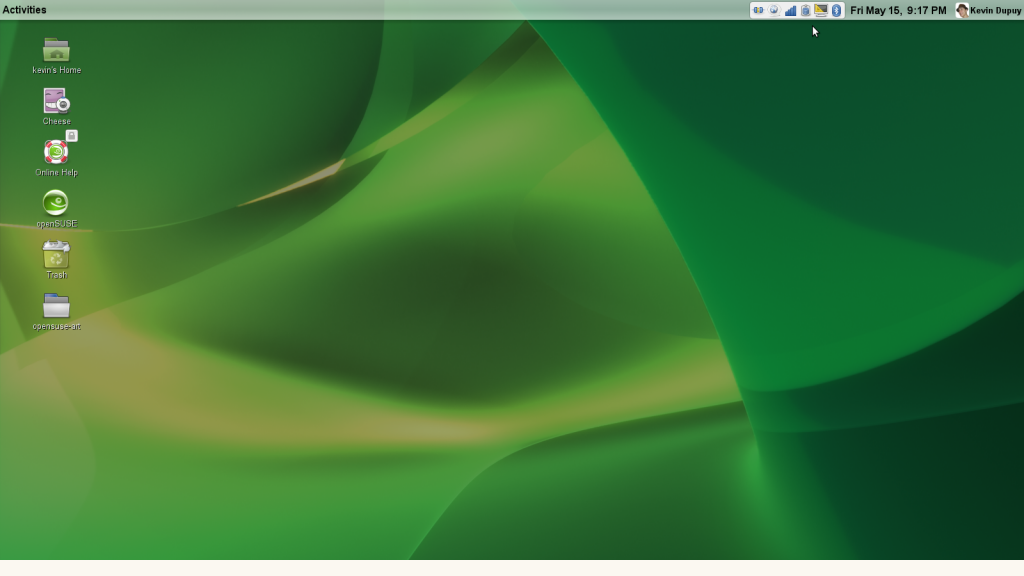
GNOME Shell Desktop
Note the Activity menu and the specially-capulated notification area. Good stuff. I al so like the stylized panel, but I don’t like it at the top. When openSUSE adopts GNOME 3, I’d like to see it moved to the bottom.
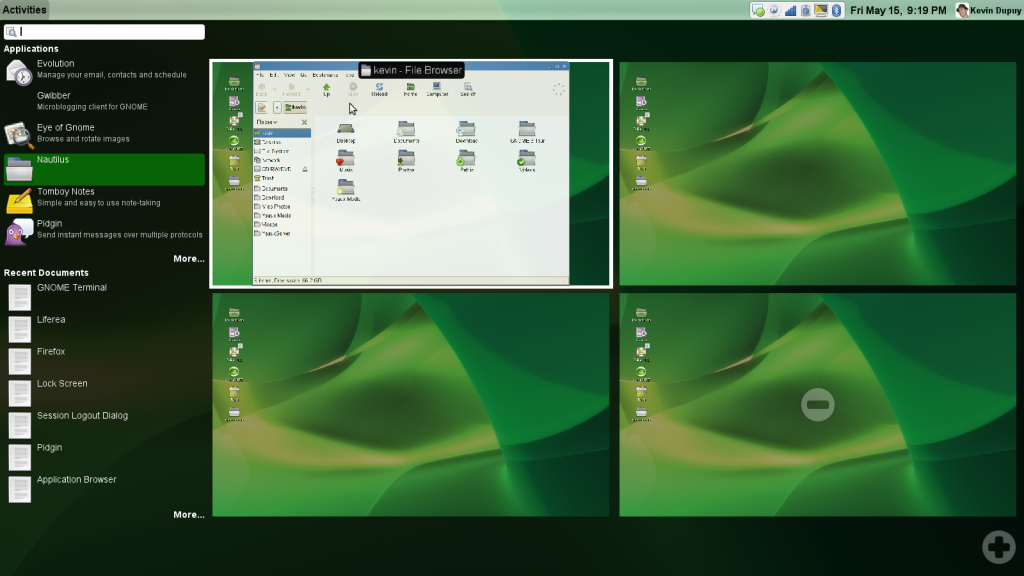
Windows being created from the Application Launcher
Clicking on the Activity menu opens this menu. The desktop shrinks into a side (and you can create or remove as many as you wish, which is seriously awesome), and opens the most recent Applications and documents (I think). If you wish to open an application, double-click or drag the icon onto the desktop you wish it to open to.
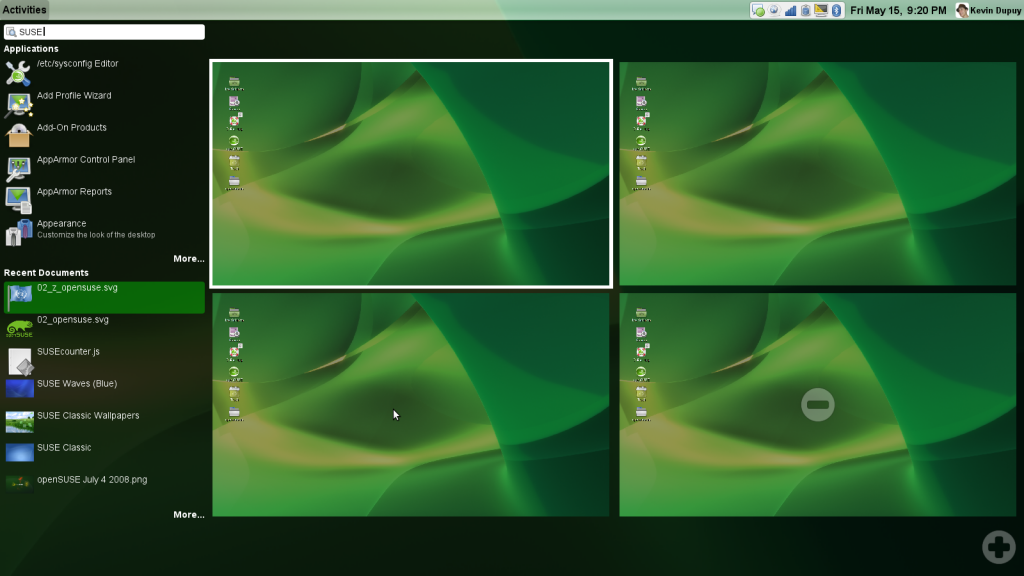
Search
Here I did a simple search for SUSE. Applications and documents that matched that search pop up (although I’m not sure what indexing service that is, I’m relatively sure it’s not Beagle, openSUSE’s desktop search indexer).
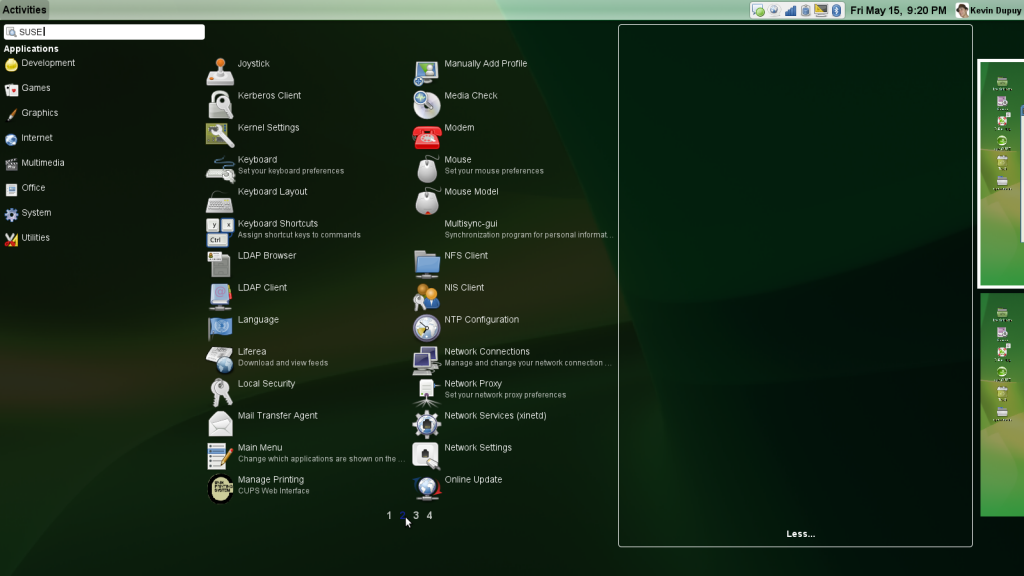
Full search results shown
Here’s an expanded view of the search for apps with SUSE. The desktops slide out of the way, and a multi-column (and page) view pops up. To open, drag an icon over to the right (onto the desktop).
Overall, I like it. Combined with the new stuff coming next year in GNOME 3, this could be quite an interesting release. One of the most important things to note is that this interface seems incredibly tailored toward netbook’s small screens.
What do you think?



