squidview
squidview is one of the software, I’ve always build and installed on each squid proxy server I build for me or customers. It’s small, stable, and usefull. So it was a clear real nice candidate to be use to improve my obs and packager skiil.
I would like to thanks T1loc, yaloki, mrdocs, coolo, alin, and all others great packagers around, for helping and teaching me during the process.
Introduction
Squidview is an interactive console program which monitors and displays squid logs in a nice fashion, and may then go deeper with searching and reporting functions.
(If you don’t know what squid is or does this program is probably not for you.)
To use squidview you must at least have read access to squid’s access.log file. You may need to see your administrator for this. Squidview uses this text log file for all operations. It does not generate its own database for tasks.
homepage www.rillion.net/squidview
Features
Squidview has a number of functions. Navigate the log file with the cursor pad keys, jump to a certain day or switch to a different log file. Search for text or large http/ftp requests.
Put squidview into monitor mode: see the latest activity updated every 3 seconds (this is light on cpu load).
Reports can be generated listing the heavist Internet users and the most popular visited sites. See how many cache hits squid makes to save network traffic.
Squidview is released under the GPL.
Examples / Usage
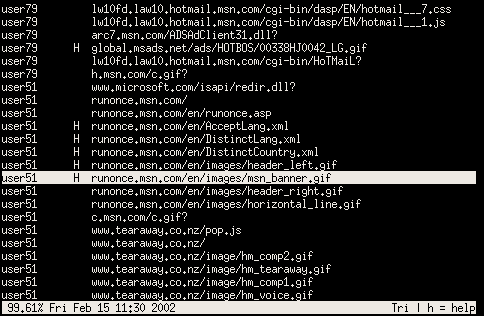
The selected line shows a request made for a .gif at the shown time. As luck would have it, the 'H' indicates a cache hit 🙂 In this mode user traffic can scroll by.
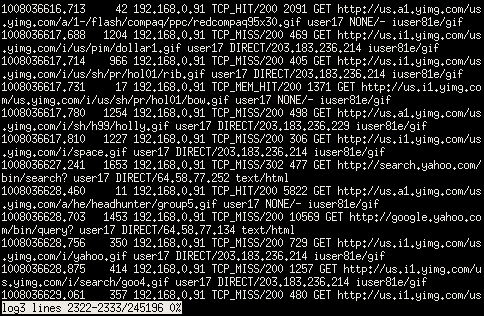
What the above would be if viewed with less.
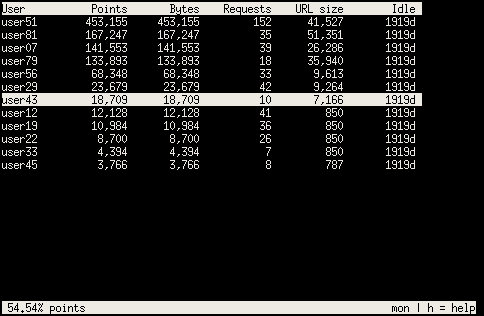
A tally of all users against the bandwidth they used. Kept current in near real time.
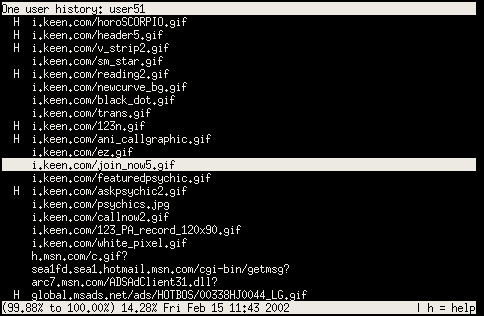
A quick investigation into the recent history of one user.
Installation / Repositories
I’ve just made a submit request against openSUSE_Factory to get it included directly, but in the meantime, you could install it from the repository server:proxy as many other useful & related packages
For example adding the repository under openSUSE_Factory
zypper ar -c -f -n "server:proxy" http://download.opensuse.org/repositories/server:/proxy/openSUSE_Factory "server:proxy" zypper in squidview
Builds available for :
The package is build successfully against : SLES10, SLES11, openSUSE 11.3 to Factory
Have Fun!

 On this week the leading KDE developers met
On this week the leading KDE developers met 